Business Against Cyber Threats: Business Against Cyber Threats: In an era where businesses are increasingly reliant on technology, the threat landscape of cyber attacks continues to evolve. For many organizations, the answer to fortifying their digital defenses lies in Managed IT Services.

This blog explores the critical role these services play in safeguarding businesses against the ever-growing menace of cyber threats. We’ll also delve into how In System Tech, powered by ArgusDNA., Integral Systems, and Pixel Crafters, offers tailor-made solutions to ensure the security of your business. We can discuss more regarding “Business Against Cyber Threats”.
Introduction:
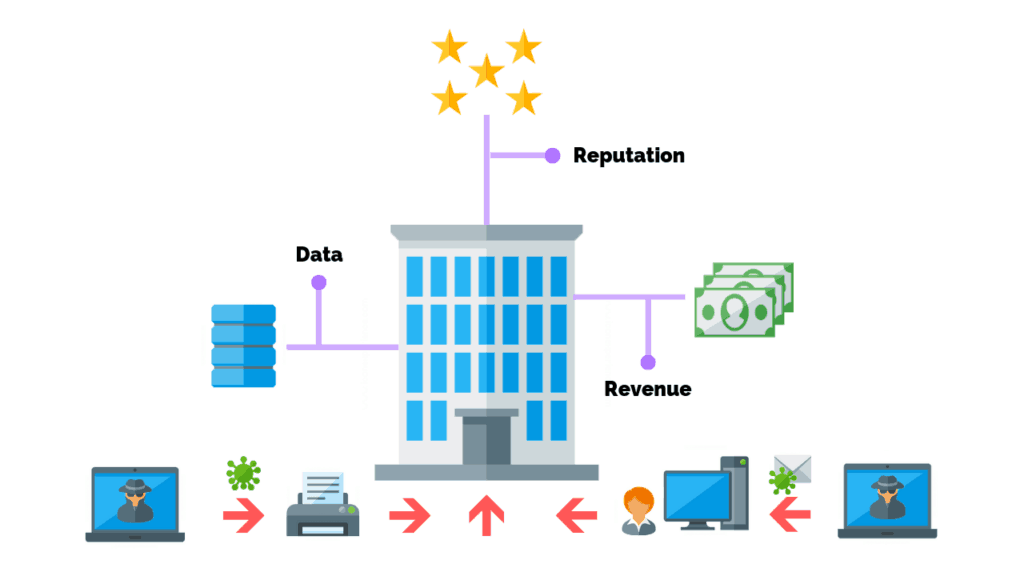
The digital landscape has opened up new possibilities for businesses, but it has also exposed them to unprecedented cyber threats. Managed IT Services emerge as a comprehensive solution, providing businesses with the expertise and tools needed to combat these threats effectively.

Read More:
Navigating the Landscape of Cyber Threats
1. Ransomware Attacks
Ransomware has become a ubiquitous threat, holding businesses’ sensitive data hostage. Managed IT Services employ advanced security measures to detect and prevent ransomware attacks, ensuring that your business remains operational and resilient.
2. Phishing and Social Engineering
Cleverly disguised phishing attempts and social engineering tactics can trick employees into divulging sensitive information. Managed IT Services not only implement robust email filtering but also conduct regular training to enhance employee awareness, fortifying your business against these deceptive tactics. We can discuss some more regarding “Business Against Cyber Threats”.

3. Data Breaches
The consequences of a data breach can be severe, ranging from financial losses to reputational damage. Managed IT Services implement encryption, access controls, and continuous monitoring to prevent unauthorized access and mitigate the risk of data breaches.
In System Tech: Your Cybersecurity Ally
1. Advanced Threat Detection
In System Tech leverages cutting-edge technology for advanced threat detection. This proactive approach identifies potential threats before they can inflict harm, ensuring that your business stays one step ahead of cybercriminals.
2. Regular Security Audits
Cyber threats are dynamic, and so is In System Tech’s approach. Regular security audits are conducted to assess vulnerabilities and implement necessary updates, creating a robust defense mechanism tailored to your business’s specific needs.
3. 24/7 Security Monitoring
Cyber threats don’t adhere to a 9-to-5 schedule, and neither does In System Tech’s security monitoring. With 24/7 vigilance, the team ensures that any potential security incidents are detected and addressed promptly, minimizing the impact on your business.

Q&A Section
Q: How quickly can In System Tech respond to a cybersecurity incident?
A: In System Tech’s rapid response protocol ensures that cybersecurity incidents are addressed promptly, minimizing downtime and potential damage.
Q: Can businesses with limited budgets afford In System Tech’s cybersecurity solutions?
A: In System Tech offers scalable cybersecurity solutions, making them accessible to businesses of all sizes and budgetary constraints.
Q: How often does In System Tech conduct security training for employees?
A: Security training is an ongoing process at In System Tech, with regular sessions conducted to keep employees informed about the latest cybersecurity threats and best practices.
Q: What measures does In System Tech take to protect businesses from emerging cyber threats?
A: In System Tech stays abreast of emerging cyber threats through continuous education, collaboration with cybersecurity communities, and proactive research and development.
Q: Can In System Tech’s cybersecurity solutions integrate with existing IT infrastructure?
A: Yes, In System Tech’s cybersecurity solutions are designed to seamlessly integrate with existing IT infrastructure, providing comprehensive protection without disruption.
Q: How does In System Tech ensure the confidentiality of sensitive business data?
A: In System Tech employs encryption, access controls, and other advanced measures to ensure the confidentiality of sensitive business data, mitigating the risk of unauthorized access.
Conclusion
Cyber threats are a constant and evolving challenge for businesses, making robust cybersecurity measures indispensable. Managed IT Services, exemplified by In System Tech, offer a shield against these threats, ensuring that your business’s digital assets remain secure. By deploying advanced threat detection, conducting regular security audits, and providing 24/7 monitoring, In System Tech stands as a reliable ally in the ongoing battle against cyber threats.


