Just what exactly is malware?
What exactly does “malware” stand for?
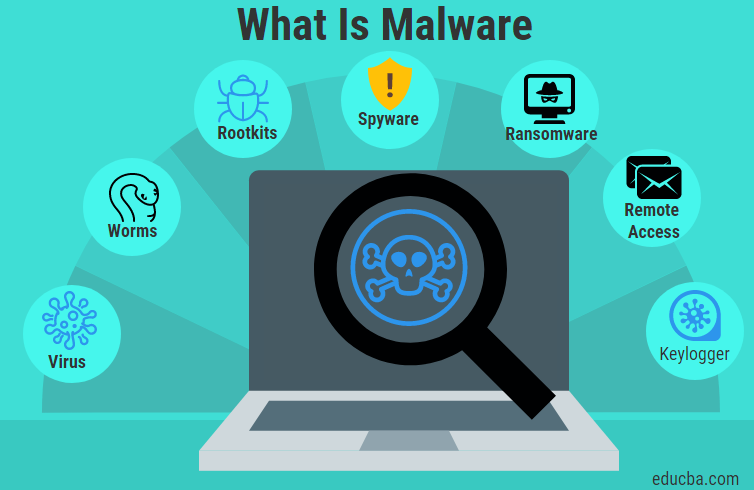
what exactly is malware: Malware, often known as malicious software, refers to any application or file that has been designed to cause damage to a computer, network, or server.
Malware is pesky software that secretly infiltrates computers and networks with the intention of doing harm and destroying them. The term “malicious software” is sometimes abbreviated to “malware.” Viruses, worms, Trojan viruses, spyware, adware, and ransomware are all examples of prevalent types of malicious software (malware). We will discuss more about what exactly is malware.
Check What exactly is malware, Types of malware Examples of malware, also How to prevent malware Best Details
Admin insystem Tech
In most cases, companies place their emphasis on preventative tools in an effort to stop breaches. Companies might give themselves the impression that they are protected if they secure the perimeter. However, more sophisticated malware will inevitably find its way into your network in the long run. We will discuss more about what exactly is malware.
As a consequence of this, it is absolutely necessary to implement technologies that are capable of continuous monitoring and locating malware that has circumvented perimeter protections. Multiple layers of security, in addition to high-level network visibility and intelligence, are required in order to provide adequate protection against modern malware.

Computer viruses, worms, Trojan horses, ransomware, and spyware are all examples of different types of malware. These harmful applications will take sensitive data, encrypt it, and delete it. They will also change or hijack fundamental computing capabilities, and they will monitor the computer activities of end users. We will discuss more about what exactly is malware.
What does malware do?
Malware is software that is designed to infect computers and networks in order to cause damage to such systems and/or to the users of those systems.
This harm may manifest itself in a user or endpoint in a different way depending on the sort of malware and the objective it seeks to achieve. Malware can have a relatively moderate and harmless effect in some situations, but in others, it can have extremely negative consequences. We will discuss more about what exactly is malware.
No matter the technique, malicious software is meant to take advantage of a device’s vulnerabilities to the detriment of its owner, the user, and to the advantage of the hacker who created and/or is responsible for distributing the malware.
How can people end up getting infected with malware?
The distribution of malware that can infect devices and networks is carried out by its creators through a range of both physical and virtual channels. For instance, malicious programmes can be delivered to a system through the use of a USB drive, through common collaboration tools, or through drive-by downloads, which automatically download malicious programmes to systems without the user’s approval or knowledge. [Citation needed] Drive-by downloads are also another way that malicious programmes can be delivered to a system.

Phishing attacks are another prevalent method of malware delivery. In these attacks, emails that appear to be normal communications really contain malicious links or attachments that send the executable file of the malware to users who are unaware they are being targeted. In sophisticated malware operations, the use of a command-and-control server is common. This server enables threat actors to connect with infected systems, steal critical data, and even take remote control of a device or server that has been hacked.
Emerging forms of malware are equipped with innovative evasion and obfuscation strategies that are not only aimed to trick users, but also security administrators and antimalware programmes. These strategies are designed to confuse consumers. Some of these methods of evasion rely on straightforward strategies, such as the utilisation of web proxies for the purpose of concealing illicit traffic or originating IP addresses.
Anti-sandbox techniques that enable malware to detect when it is being analysed and to delay execution until after it leaves the sandbox; fileless malware that resides only in the system’s RAM to avoid being discovered; polymorphic malware that can repeatedly change its underlying code to avoid detection from signature-based detection tools; fileless malware that resides only in the system’s RAM to avoid being discovered; polymorphic malware that can repeatedly change its underlying code to avoid detection from signature-based detection tools; polymorph
What are the various forms that malicious software can take?
Different forms of malicious software each exhibit distinctive qualities and attributes. The following are examples of several types of malicious software:
• A virus is the most common form of malware that is capable of executing itself and spreading by infecting other programmes or files. • A worm can self-replicate without a host programme and typically spreads without any interaction from the malware authors. • A Trojan horse is designed to appear as a legitimate software programme in order to gain access to a system. Trojans are able to carry out their harmful duties once they have been activated, which occurs after installation.

• Without the user’s awareness, spyware gathers information and data about both the device and the user, as well as monitoring the user’s activity on the device.
• Ransomware infects a user’s computer and encrypts their data after taking control of it. After then, the perpetrators of the attack will demand a ransom payment from the victim in exchange for decrypting the data on the system.
• A rootkit grants the user access to the victim’s system that is equivalent to that of an administrator. When the software has been successfully deployed, it grants threat actors privileged or root access to the machine.
• A virus that opens back doors or a remote access Trojan (RAT) clandestinely instals a backdoor into an infected computer system, allowing threat actors to get remote access to the system without alerting either the user or the security programmes that are running on the system.
• Adware monitors a user’s browser activity as well as their download history in order to present pop-up or banner adverts that are designed to persuade the user to make a purchase. For instance, in order to more precisely target advertising, an advertiser may employ cookies to keep track of the websites that a user visits.

• Keyloggers, which are also known as system monitors, are capable of tracking practically all of a user’s activity on their computer. This includes programmes, emailed messages, web pages that have been opened, and keystrokes.
How to identify malicious software
Users may be able to determine the presence of malware if they observe unusual behaviour, such as the sudden loss of disc space, unusually slow speeds, repeated crashes or freezes, or an increase in unwanted internet activity and pop-up advertisements. Malware can also be detected if there is an increase in the number of pop-up advertisements.
It is possible to identify and eliminate malware on a device by installing antivirus and antimalware software on the device. By performing routine system scans, these technologies can either provide security that is active in real time or detect and eliminate malware.
Anti-malware software developed by Microsoft and incorporated in the Windows 10 operating system (OS) as part of the Windows Defender Security Center is referred to as Windows Defender, for example. Windows Defender provides protection against a variety of potential dangers, including spyware, adware, and viruses. Users have the ability to set automatic “Quick” and “Full” scans, in addition to setting alarms with low, medium, high, or severe priority.
Secure your computer from “malware” with us.
Pro Group Networks LLC offers the best Computer Virus and Malware Removal Services, whether you require them for your home or your business. Remote virus elimination services. If you need a virus removed, it’s easy to chat with one of our security experts over the phone or online. Contact the IT Support Guys at www.insystemtech.com Powered by Argusdna.


