What is Multi-Factor Authentication: Despite being an art form, MFA is not dependent on having a Master of Fine Arts degree (Multi-Factor Authentication). Identity and access control for your company can be strengthened with multi-factor authentication.
When it comes to thwarting cybercriminals, employees are both a company’s greatest asset and greatest weakness. By adding a second layer of protection, you may significantly increase the security of both your employees and your data.
If one layer of defence is breached, there is still another one in place thanks to multi-factor technology. Brute force and dictionary attacks can be used to crack conventional usernames and passwords. The MFA strengthens credentials.
What precisely is MFA, and how can it safeguard you? How are MFAs established? Are there any drawbacks to it?
What is MFA?
The inclusion of elements outside of conventional credentials to secure authorization is known as multi-factor authentication.

Using their usual username and password, employees log in. The second phase of authentication is then successful when they are opened. Anything from a retina scan to a randomly generated passcode might be the second authentication element. Later, we’ll talk about alternative MFA strategies.
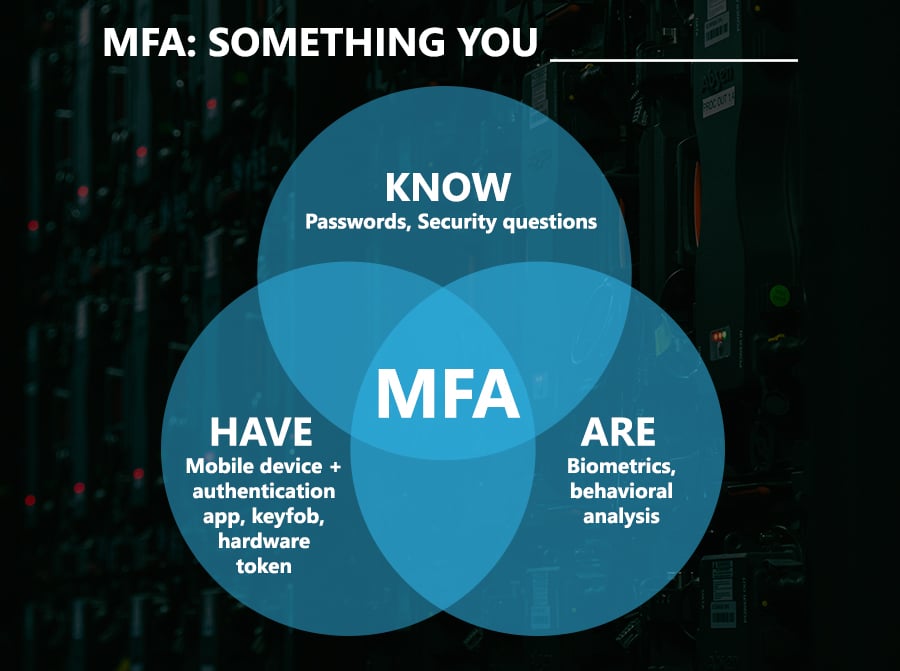
These methods are typically divided into three groups. anything about the individual—something they own, something they are. Every level of authentication should, ideally, belong to a separate category than the one before it.
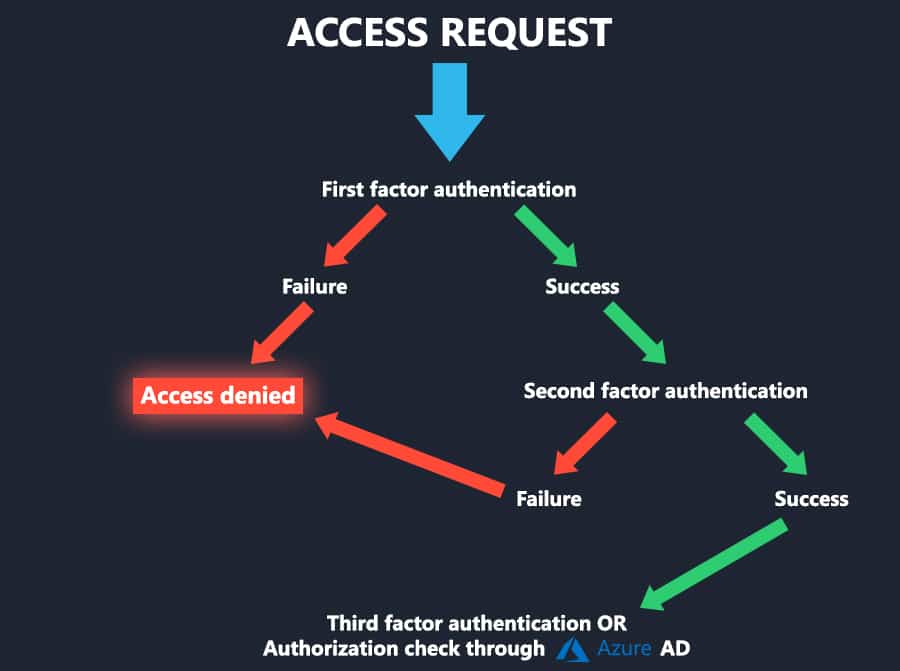
MFA is no longer merely a suggestion for some companies. MFA must be used “for all remote network access that starts from outside the network to a Card Data Environment (CDE)” in order to comply with the Payment Card Industry (PCI) Data Security Standard. According to PCI-DSS version 3.2, “full administrative access” must be used.
Starting in 2005, the Federal Financial Institutions Examination Council started advising employing various factors when gaining access to online financial information.
Difference between MFA and Two-Factor Authentication
Remember that MFA includes the archaic “Two-Factor Authentication” while discussing MFA. When MFA was first implemented, when the majority of enterprises were merely enhancing their security with one additional element, two-factor was utilised.
Swiping your debit card, for instance, counts as “something you have” when you use an ATM. “Something you know” is when you enter your pin. Two-factors.
Read More:
“Multi-factor authentication” has become the accepted word. This is as a result of more businesses regularly including biometrics, location, and/or time as a third factor.
Authentication vs. Authorization
Despite the fact that they sound similar, authentication and authorization are really distinct.
Verifying someone’s identification is done through the process of authentication. Verifying someone has access to a file, data, etc. is known as authorization.

Always authenticate before you authorise. You would want your security officer to verify the person’s identity before allowing them to enter your building, right? The guard can provide entrance after the person authenticates.
You should think about using access controls to decide who is allowed to view a certain piece of data. Once you know what each person has access to, you can set up their authentication so that they can be recognized.
Kinds of MFA
There are three basic categories for authentication elements, as we previously mentioned: what the person knows, has, and is.

Additionally, there are new elements at work. A fantastic technique to authenticate a person is to know where they are and when they are attempting to log in.
Let’s take a deeper look.
This is a time-tested classic. The question has always been the same whether you are signing into your email, a secret document, or a super-exclusive club.
How do I find the password?
The classic “something you know” authentication is demonstrated here. If you know the password, you belong to a select club.
Passwords can be cracked, nevertheless, if there are enough guesses and the means to generate them more quickly than you can count. These days, a password is insufficient. It must be lengthy, contain special characters, upper- and lower-case letters, not be a word from the dictionary, among other requirements. We can discus more about What is Multi-Factor Authentication.
It is understandable why you require more than a password to stay safe. Dictionary attacks and brute force are one thing, but perhaps they are not even necessary. Poor passwords are sometimes used by employees. We can discus more about What is Multi-Factor Authentication.
Although they can add a second layer of “something you know,” answers to personal security questions are still vulnerable to the same kinds of assaults. There are numerous variations on the terms “first automobile,” “street you grew up on,” and “mother’s maiden name.”
Therefore, if cutting-edge technology can guess your password, they can guess your security question as well. Keep up with all password security recommended practices, such as choosing unique passwords for every account and utilizing a password manager. We can discus more about What is Multi-Factor Authentication.
Use a different type of factor even better.
Do you recall how much time you wasted in your favourite video game trying to find the dungeon key? How about all the frustration you felt while searching in vain until you discovered it?
Consider your second element to be the dungeon key. You are the key’s keeper this time around, saving yourself the frustration of having to look for it. It functions in the same way as a regular key, a keyfob, or a swipe-able access badge. We can discus more about What is Multi-Factor Authentication.
Your smartphone and an OTP will typically be the key in the case of your IT (OTP). You will either receive your OTP by text message or email, or it will be produced via an authenticator app. This is frequently done as well if you want to reset a password.
The term “software tokens” can also be used to describe authenticator apps.
Even though you already know your OTP, you can only access it with a possession. similar to that smartphone
Things You Are/Biometrics.
The use of human features to grant access is known as biometrics. Consider the typical methods used by certain cellphones to unlock them nowadays, such as your fingerprint or face.
Instead of using face scans, agencies who wish to take things a step further can use iris or retina scans. Hand geometry, earlobe geometry, and voice authentication are additional physical characteristics that are utilised in biometrics. We can discus more about What is Multi-Factor Authentication.
Behavior analysis is one newly popular application of biometrics for authentication. This is the way you are, not merely a tangible representation of “things you are.”
Consider a scanner for digital signatures. Scanners check a digital representation of your handwritten signature for authenticity against other examples.
A typing analysis looks at how you type rather than what you type. How quickly can you type? What’s the order? What recurring trends do you see as you type particular word groups?
As absurd as it may appear, this behavior can be utilized to verify who you are. The same can be done with the way you move the cursor on your computer screen. These more advanced biometric technologies are mostly utilized in the finance industry.
Time and Location
The same laws that regulate almost everything else also apply to your IT access.
Do you recall the day you entered a bar in Tokyo, purchased a few drinks, and then left right away to enter a shop in New York City to purchase an umbrella? Most likely not. It is not possible.
This is why your bank contacts you to resolve any overlapping transactions as soon as they are noticed by them. You may protect your data in the same way that your bank does with your money.
Any cybersecurity provider worth its salt will prevent an account from attempting to authenticate over two physically impossibly long distances in an unreasonable amount of time. We can discus more about What is Multi-Factor Authentication.
Why Use MFA?
Every time you require a credential, there is a lot on the line. That is the primary reason you are guarding something. Enabling MFA is simple, that much is true.
Over time, billions of credentials are stolen. The evidence is unmistakable: cybertheft occurs frequently. There are several simple methods for cracking passwords.
Not to add that passwords are frequently just given away. One of the most effective cyberattacks does not even require password cracking; instead, it uses phishing emails.
Because of this, your organization’s workforce needs cybersecurity training from the top to the bottom. We can discus more about What is Multi-Factor Authentication.
Your staff are your biggest cybersecurity liability, so whether you’re a CEO or business owner, you need to take it into account. Even when tight password restrictions are enforced, employees will perform the absolute minimum. One credential is all it takes for a cybercriminal to access your data, and at least one member of your staff is likely to fall for a phishing email.
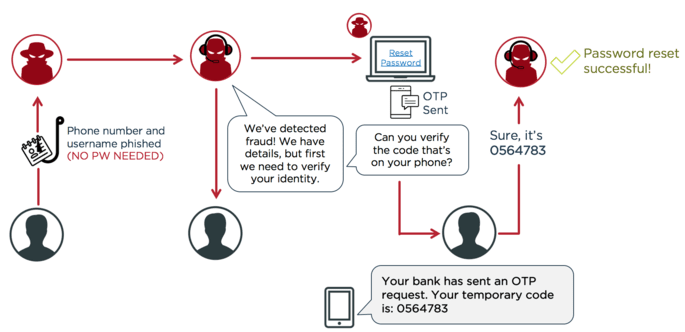
Bad actors that steal a credential will encounter a second barrier by adding a second authentication factor. They won’t get the access they want without an employee’s possession or biometrics.
If remote workers utilise a non-corporate or unmanaged equipment, it poses a risk as well. These gadgets frequently access your data from a distance, but they lack the company computers’ security features. Cybercriminals have a backdoor to your data if any device, network, or application is not adequately protected. We can discus more about What is Multi-Factor Authentication.
Overall, MFA is a reinforcement of the security measures you already have in place. The addition of tertiary and secondary elements is only helpful. You need a lock if your warehouse has a front door. What if, like a smartphone, you also included a fingerprint or facial scanner?
How many times a day do you check your phone? You can open it that many times, how simple is that? Security in a straightforward form—that is the essence of MFA. Capacity of MFA.
A programme called “Modlishka,” which utilised a reverse proxy to get around MFA, was made public in the early months of 2019 by a Polish cybersecurity researcher named Piotr Duszyski. To demonstrate that multi-factor authentication cannot eliminate all threats, he made the technology available to the public.
It’s critical to realise that no security mechanism is impenetrably effective. No matter how strong your defences are, being aware of your shortcomings is equally important. Sadly, MFA has drawbacks and is susceptible to attack. We can discus more about What is Multi-Factor Authentication.
The largest drawback is that, even when security is configured to demand two factors to log in, account recovery frequently just calls for one.
There is a risk that one of your variables, the use of a mobile device, can restrict access for some users.
Smartphones aren’t always 100 percent trustworthy. It’s possible that the battery is dead or that the local service is subpar. You will lose access to your mobile-based authorisation factors if you are unable to use the internet for either of these reasons.
If that mobile device is stolen or lost, the situation just gets worse. A potential cybercriminal has compromised that factor of authentication if they are able to intercept a token or OTP.
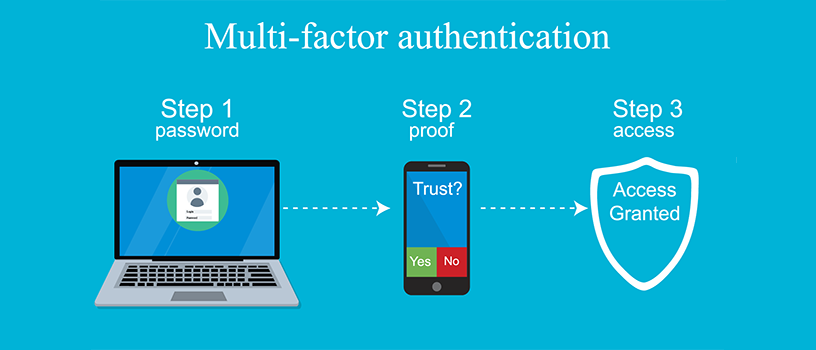
- If a user falls victim to a phishing scam, they can experience the same outcome. There is a possibility that they provide both their login and password and an OTP that can be used right away if they are sent to a fake URL. We can discus more about What is Multi-Factor Authentication.
- Credentials can be intercepted by further man-in-the-middle attacks:
3. Man-in-the-browser – A hacker deliberately seizes control inside a web browser, similar to a man-in-the-middle assault. We can discus more about What is Multi-Factor Authentication.
4. SIM cloning: In this scenario, a hacker would gain control of the SIM card of a mobile device, clone the software on it, and take over the device’s operations.

5. IMSI-catchers – Picture a man-in-the-middle assault, but instead of utilising a browser or operating system, use a mobile phone tower. used to intercept OTPs or other tokens by mobile devices.
These risks demonstrate why biometrics are being utilised more frequently. Which sounds easier, stealing a fingerprint or stealing a smartphone? Instead than imitating someone’s face, retina, or conduct, how about faking. We can discus more about What is Multi-Factor Authentication.
Using a hardware token that adheres to the universal second factor (U2F) standard is currently the best option to strengthen your second factor.
How to make MFA simpler
Access will take longer because of the additional security measures. Your users may find this frustrating, but it will be worthwhile in the long run.
Here are some strategies for streamlining MFA while maintaining robust cybersecurity.
solitary sign-on (SSO)
SSO is a service that enables users to sign on to several applications with just one set of credentials. When a user submits an authentication request, SSO serves up a single set of credentials across all required apps, acting as a middleman. Users won’t need to reenter authentication after signing in. We can discus more about What is Multi-Factor Authentication.
Users who frequently forget their passwords and have to change them feel less frustrated thanks to SSO. In this situation, they have fewer things to remember and forget less frequently. There are less potential for phishing attacks when there are fewer places to submit credentials.

Though, with SSO, it’s important to remember that if an attacker gains access to one app, they probably have access to all of them. It will still be essential to add another element. We can discus more about What is Multi-Factor Authentication.
Push Authentication
Push notification authentication is a feature of most authenticators. Use this option to avoid requiring users to memorise an OTP, log into an authenticator app, then input it elsewhere.
The user only needs to click “confirm,” just like with any other notification they receive on their phone. You likely just used a biometric to validate your smartphone if the push authentication is sent to it.
Push authentications make the process of authenticating simpler. They occasionally add even more protective elements.
Flexible MFA
With adaptive MFA, context is used to judge whether a user authenticates against a variety of actual scenarios. Recall the preceding illustration of making a transaction in Tokyo and New York City in a matter of minutes?
That demonstrates adaptive MFA in action. To demonstrate that an authentication is untrue, a set of rules—in this case, the laws of physics—is applied.

Based on their operations, businesses might establish their own guidelines to determine a suspicious login attempt.
Here is a simple example:
Imagine all of your users are required to work from the same physical workplace, are not allowed to work from home, and never leave on business vacations. The company has the right to refuse authentication from certain areas or IP addresses. Yes, this may appear excessive, but it will unquestionably prevent anyone who is not a staff member from accessing the data. We can discus more about What is Multi-Factor Authentication.
You can restrict authentication to a specific OS if everyone in your firm uses the same standard-issue PC. Authentication will fail if a user attempts to sign in using an Apple OS while your business only supports Microsoft.
Along with other criteria, these examples adjust to your company’s needs and add an extra degree of security. Organizations may customise their MFA to fit any scenario with the right setup.
Microsoft 365 MFA
You are now prepared to configure multi-factor authentication in the Microsoft 365 cloud for your company. But how do you go about it? Which alternatives do you have?
It’s simple to set up MFA with Microsoft 365. Select users through your Microsoft 365 interface. Then select the users for whom you want to impose MFA by clicking the multi-factor authentication option. To achieve this, you must be a global administrator.
Ideally, MFA would be required of all users by the global admin. The most crucial step, however, is the next one: setting up your conditional access settings using Azure AD.

Before making more precise adjustments, you can enable the default security configuration for Microsoft Azure AD.
For more information on the kinds of actions you can limit after users successfully authenticate, be sure to consult our guide on access restrictions.

You can get assistance from IT Support Guys setting up your MFA and access controls in Google Workspace or Microsoft 365. For less than the cost of one IT hire, we can manage your cybersecurity in a proactive manner. We can discus more about What is Multi-Factor Authentication.
Give us a call today at +18885065226
If you need to improve computer performance for your small business, contact the IT Support Guys at www.insystemtech.com right now. In addition to other IT services, we offer desktop support to ensure that you get the most out of your hardware. Dial +18885065226 to speak with a specialist right immediately. Powered by ArgusDNA

