Cybercriminals, before launching an attack, will often assess the organization’s defenses to see where the weak spots are. The term “system” can refer to a website, piece of software, or connected device. Therefore, strong cyber defenses are essential. Additionally, a robust endpoint security solution that safeguards all company devices should be put in place. We will discuss more about What is ENDPOINT SECURITY further in this blog.

In this blog we will Know About What is endpoint security management, What is endpoint security examples, Endpoint security vs antivirus.
Abmin Insystem Tech
Safety at the terminals
The term “endpoint security” describes the strategy of blocking off any potential entry points for cybercriminals within your organization. In most cases, it includes everything connected to your network. We will discuss more about What is ENDPOINT SECURITY further in this blog.
Endpoint protection’s primary function is to keep malicious software, such as ransomware, out of your network and thus protect your business. A reliable solution can aid in the identification, evaluation, and prevention of malware and other forms of cyberattacks.
It is important to take endpoint security seriously. It’s important to remember that it’s a crucial part of any IT infrastructure or network security plan, no matter how big your company is. We will discuss more about What is ENDPOINT SECURITY further in this blog.
Read More:
How to Clean Malware From Your Personal Computer [Guide 2023]
Endpoint Security Varieties
Some of the varied endpoint security measures are listed below.
- One, Encryption at the Endpoint
- Secondly, a forensic examination
- Thirdly, safeguarding the Internet of Things
- Electronic mail (email) entry points
- Safeguards against contamination in a quarantine
HOW DOES ENDPOINT SECURITY ACTIVATE?
Endpoint security can be set up either locally or in the cloud, depending on your company’s preference. Files that are uploaded to a network can be checked against a cloud-based database of known malware using an endpoint protection platform (EPP). Protect your company from cybercriminals by using a platform that employs machine learning in real time. We will discuss more about What is ENDPOINT SECURITY further in this blog.
Some of the more complex and sophisticated threats that can be uncovered by a solid endpoint security solution are as follows:
Malware that does not use files
Modern malware infects computers by masquerading as legitimate software. Since no file is required, it can easily evade detection by common anti-virus programs, unlike traditional malware.
Concealment flaws
Attacks that take advantage of flaws in freshly released or updated software. This is a good opportunity for them, as early detection of attacks may be impossible and developers may lack the resources to address the issue.
Attacks with a polymorphic form
Polymorphic refers to something that can take on a variety of shapes and sizes. By constantly shifting characteristics like file names and encryption keys, polymorphic attacks evade detection by security systems.
Juice jacking
Makes use of special USB ports created specifically for spreading malware. Since free charging stations might just be a disguise, using them is risky.
Just how crucial is it to have secure endpoints?
Security teams no longer need to physically be present at a single location and use a single portal in order to gain access to critical repositories and servers. Today’s more advanced state can be attributed to the persistent development of technology and the accessibility of cloud hosting.
This allows your staff, business associates, and vendors to access your network from anywhere in the world, using their own devices. While this is an advantage when running a global business, it also comes with several cybersecurity risks.
An effective endpoint security system guarantees that all potential entry points are being monitored and are prepared to be sealed.
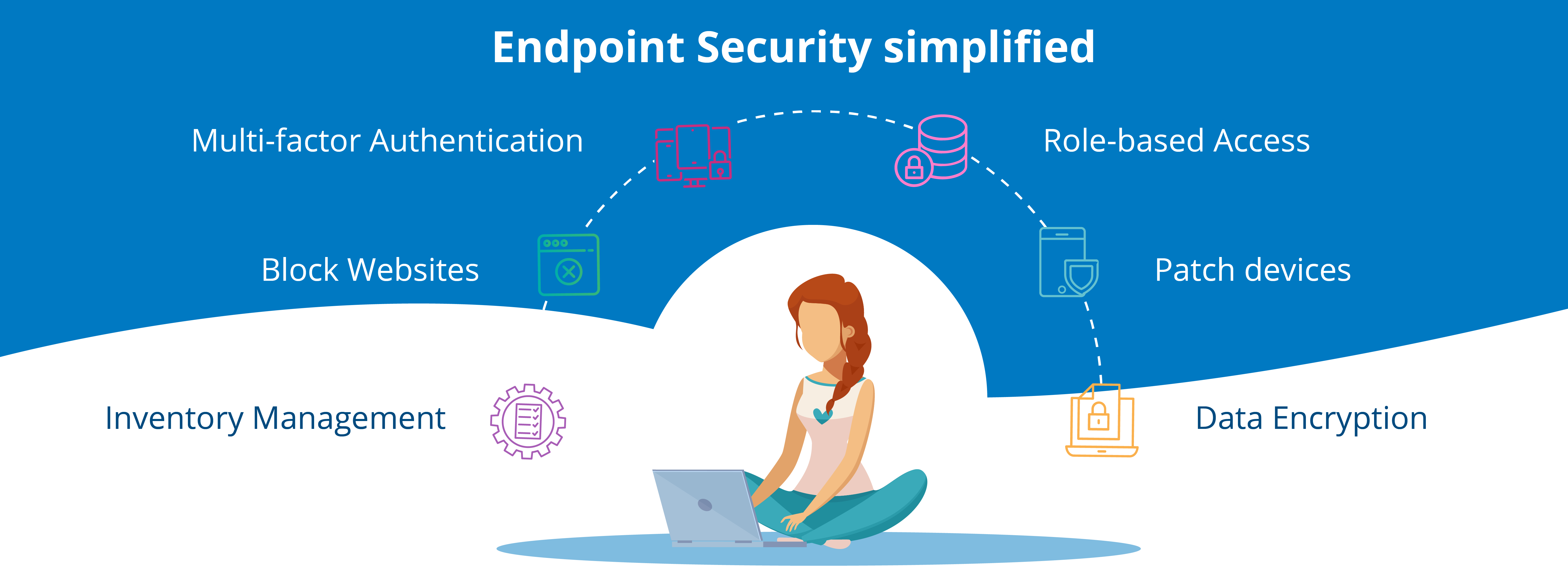
ADVANTAGES IN ENDPOINT PROTECTION THAT ITS PRIMARY ELEMENTS OFFER
The right endpoint security solution for your business requires careful consideration of several factors. Don’t be swayed by vendors who claim they can provide you with a complete suite but lack the important elements you need.

Here are some of the most essential features you need to look out for:
Device protection
Is the product optimized for mobile endpoint protection? Look for a solution that features antivirus and malware protection not just for computers but mobile devices as well.
Network controls
Your endpoint security solution should perform like an inclusive firewall that sorts through all incoming traffic and detects potential risks.
Application controls
Can the product be integrated with application servers to allow continuous monitoring and access restrictions?
Data controls
Are there tools that can help prevent data leaks and improve data security using encryption of sensitive information?
Browser protections
Go with an endpoint security solution that has a web filter option. This can help you restrict website access while connected to your network.
While traditional antivirus programs can be beneficial to your organization, they often can’t keep up with today’s ever-advancing techniques to compromise a network. That is why it’s essential to develop a solid endpoint security approach as part of your entire network security.

Get ENDPOINT SECURITY from Insystem tech Services
Our comprehensive anti-virus software services protects your files and systems from infections including worms, Trojan horses, and spyware. Insystem tech Mobile Security, Powered by argusdna. you can guard your device against viruses and other forms of malware. Over 435 million individuals place their faith in this brand.


